
Think Before You Click - Don’t Simply Trust Emails
Phishing is a common issue that businesses of all kinds can experience,…

What You Need to Know to Avoid Phishing Attacks
Phishing is a remarkably dangerous tactic used by hackers to…

The FBI is Looking to Talk to Businesses Affected by Ransomware
This past January, the Federal Bureau of Investigation issued…

Remote Work Needs to Be Secure Work…Here’s What You Can Do
Remote work has seen unprecedented adoption in the past few years.…

Password Managers Have Built-In Value
Most organizations are trying to figure out how to secure their…

You Need to Take Your Cybersecurity Seriously
Small businesses have a lot to worry about in terms of technology,…

What’s the Line Between a Security Breach, and a Data Breach?
When security breaches and data breaches are mentioned in the…
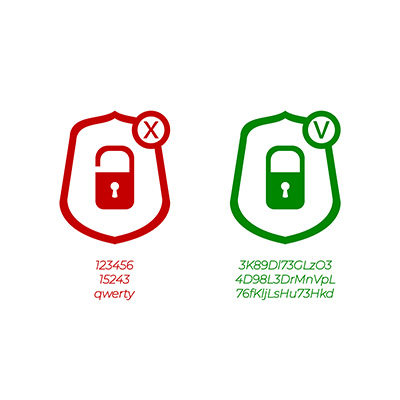
4 Simple Rules for Good Passwords
Simple passwords are just not an effective security practice,…

What is a Zero-Day Exploit?
While security researchers do their best to find security vulnerabilities…

Don’t Fall for the Google Business Profile Scam
There is a scam going around that convinces organizations to…
